What you see here are the quantum vulnerabilities lurking in blockchains.
These are systemically fatal, and since “post-quantum cryptography is ineffective,”
the entire structure must be replaced with a different algorithm.
Prioritizing clarity: we’ve used illustrations only. (Mathematical formulas have retired!)
Why is post-quantum cryptography ineffective against the blockchain quantum vulnerabilities listed here?
-- It's simple: because Shor's algorithm isn’t used --
* Post-quantum cryptography was originally designed to protect against reverse-direction attacks using Shor's algorithm, such as factoring or discrete logarithms.
If Shor isn’t involved, then PQC is irrelevant.

[Blockchain Quantum Vulnerability #1]
PoW Quantum Mining - Network monopoly using a few quantum annealers - 100% attack
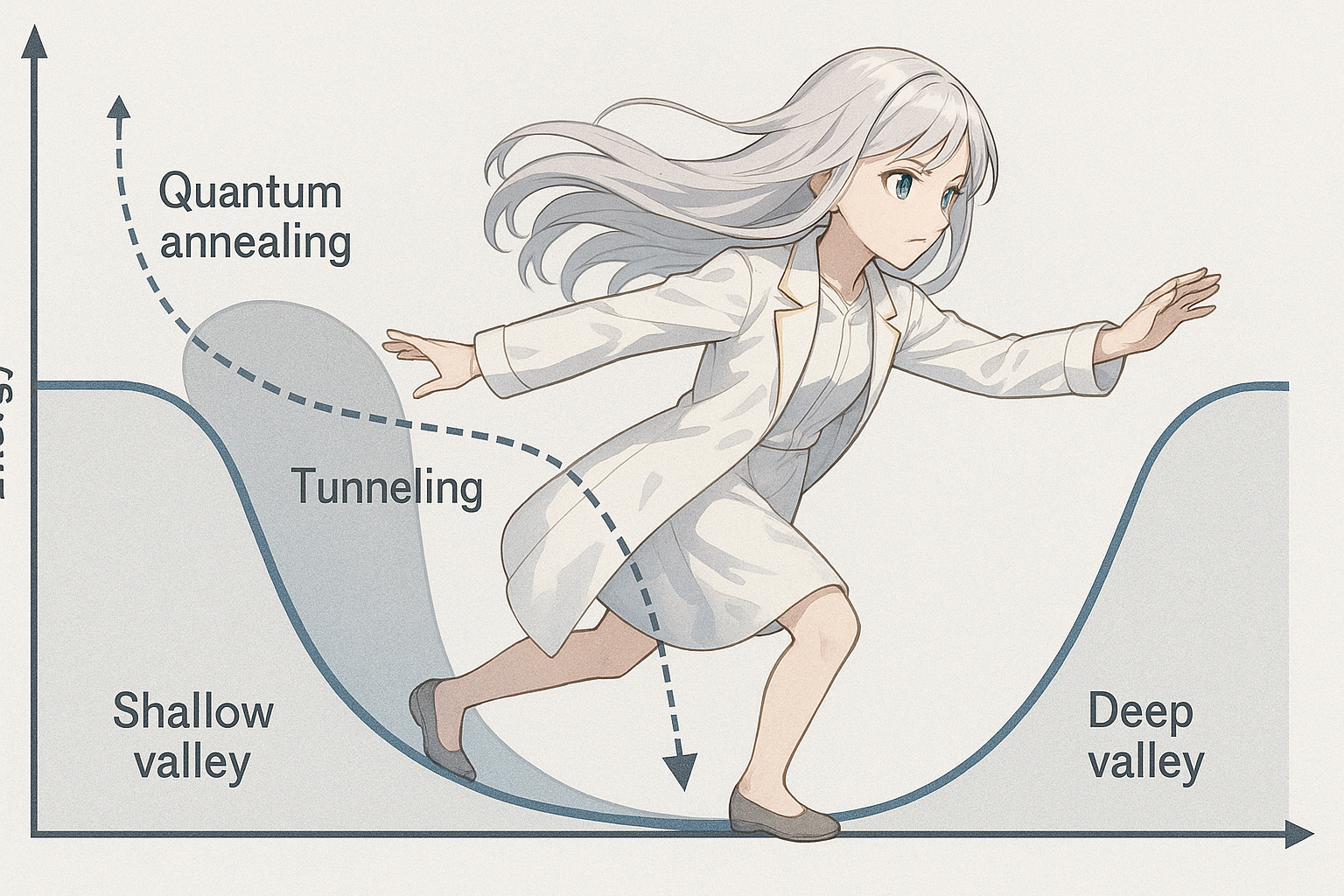
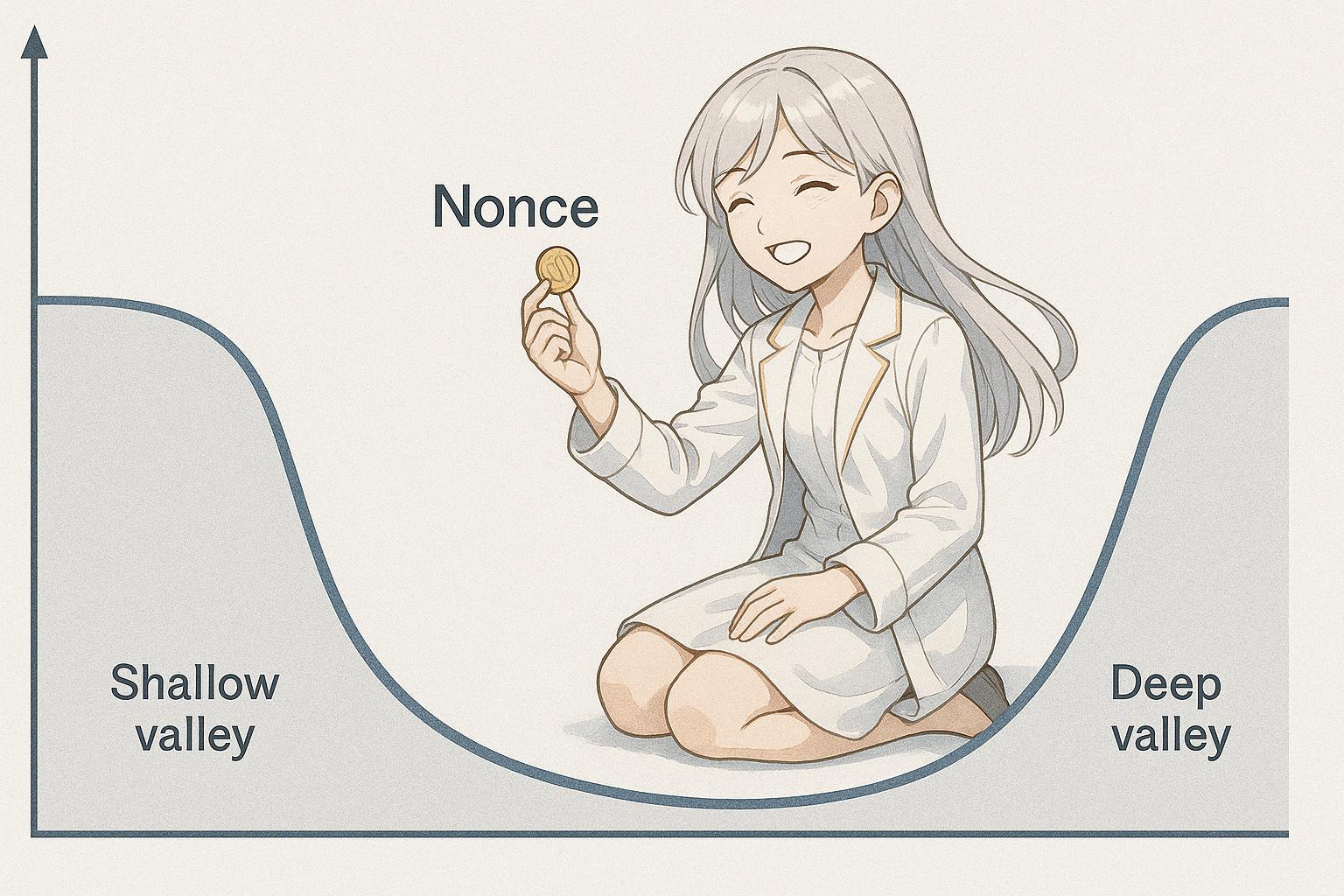
[Blockchain Quantum Vulnerability #2]
PoW Quantum Mining - Network monopoly using a single quantum gate machine - 100% attack


[Blockchain Quantum Vulnerability #3]
Quantum Secret Key Search - Catching a valid private key using a few quantum annealers

[Blockchain Quantum Vulnerability #4]
Quantum Secret Key Search - Catching a valid private key using a single quantum gate machine